Ars Technica’s gift guide for Father’s Day: Give dad some cool things
Segway Ninebot E2 Pro Scooter – $450 Fair warning: Dad will feel like a kid again…

Segway Ninebot E2 Pro Scooter – $450 Fair warning: Dad will feel like a kid again…
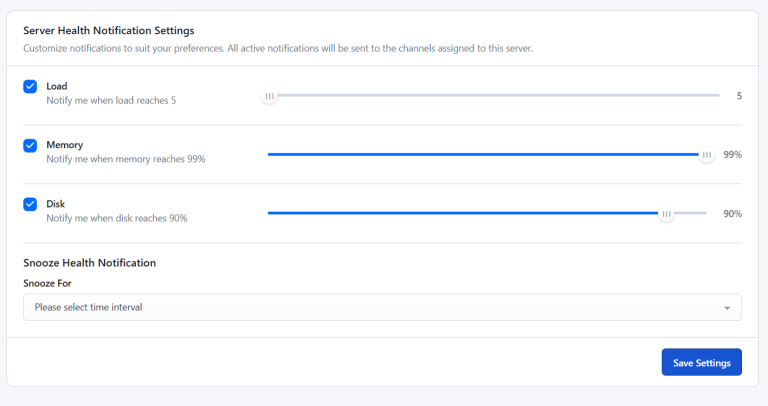
Is your WordPress site running slow, timing out, or crashing altogether? High CPU usage is often…

For years, gray market services known as “bulletproof” hosts have been a key tool for cybercriminals…
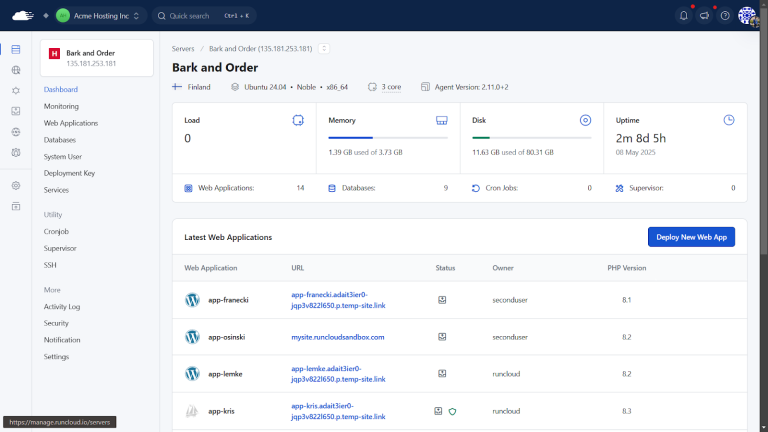
Using a VPS to host your websites provides both control and seamless scalability. However, many people…

Outside researchers can request access to VSD data by submitting study proposals to the CDC. The…
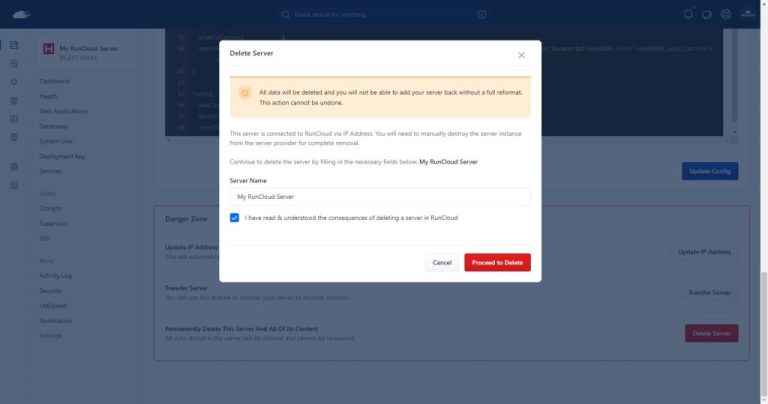
Setting up a cloud server to host your website can be a daunting task, especially if…
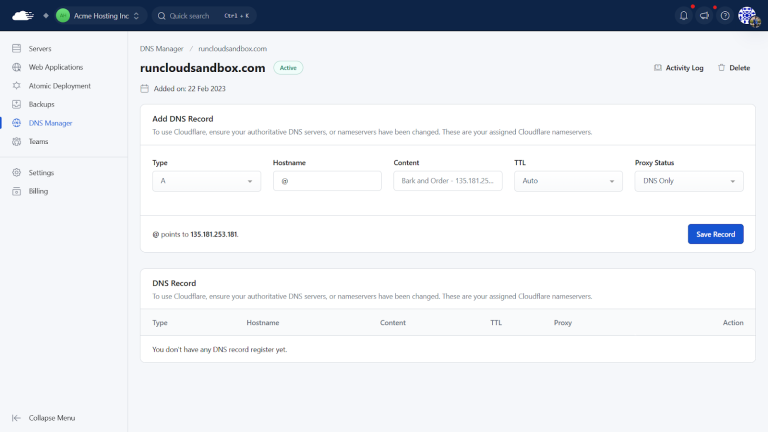
Tired of cPanel’s limits? You’re not alone. If you’ve ever been frustrated by slow performance during…
Important thing first. Ubuntu 20.04 LTS version will be reaching its end of life on 31st…
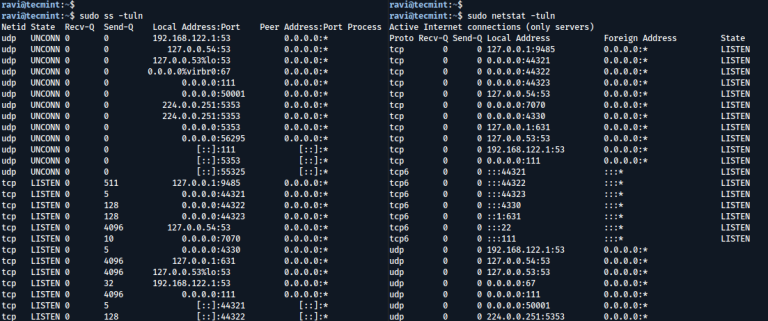
When you build a server according to your plan and requirements, you want it to run…

FTP stands for File Transfer Protocol and is one of the most widely used and standard…
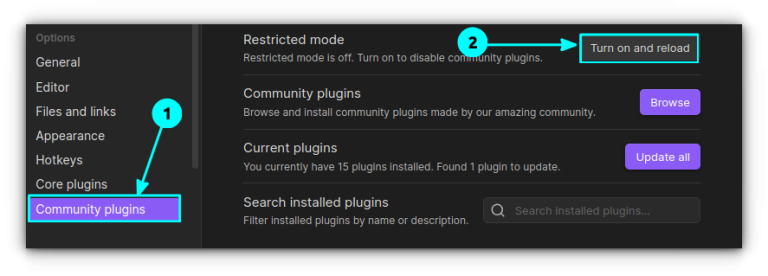
Obsidian has emerged as a powerful and flexible knowledge management tool, despite NOT being an open…

The hacker ecosystem in Russia, more than perhaps anywhere else in the world, has long blurred…
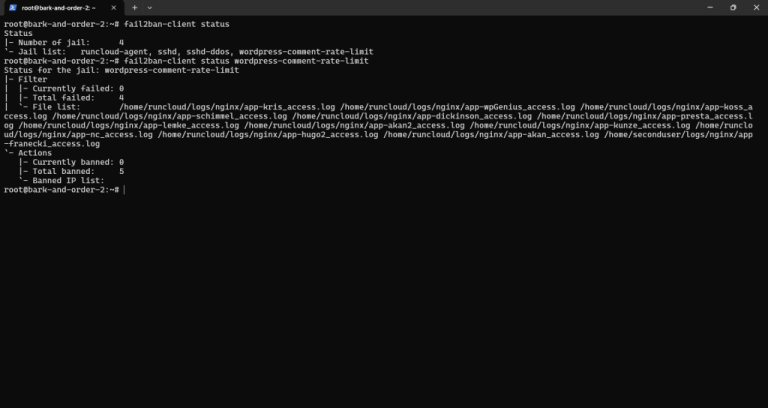
Is your website drowning in WordPress comment spam? If you’re battling endless waves of bot-generated junk,…
Welcome to Part 7 of the blog series on vSphere supervisor networking with NSX and AVI….

Biotechnology company Regeneron will acquire 23andMe out of bankruptcy for $256 million, with a plan to…

Keylogging, short for “keystroke logging” is the process of recording the keys struck on a keyboard,…