FOSS Weekly #26.09: Linux Mint Shortcuts, OpenClaw Alternatives, Ladybird's Rust Move, Super Productivity and More
I know not everyone wants to hear about AI all the time. But at this point,…
I know not everyone wants to hear about AI all the time. But at this point,…
You might have noticed that I have not shared new puzzles and quizzes for some time….
Malicious actors are doing everything at their disposal to undermine modern IT infrastructure. Some are motivated…
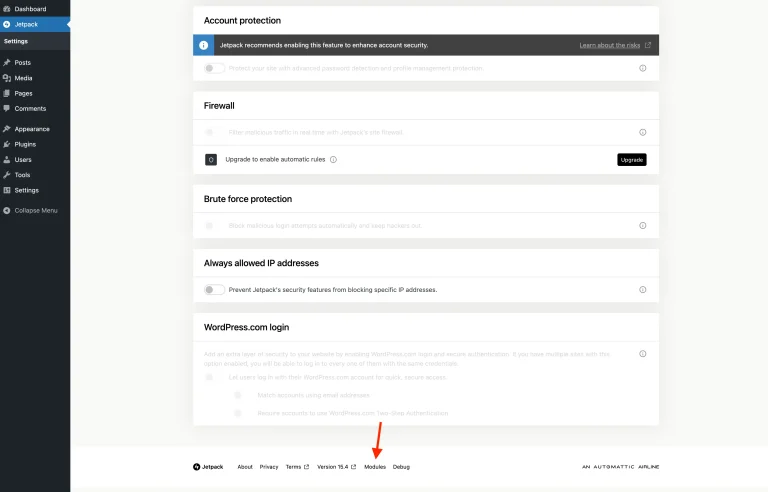
If you’re running WordPress for your own site or client projects, a managed WordPress hosting solution…
The ERR_NAME_NOT_RESOLVED is a frustrating error message that prevents you from browsing the web. The good news is…

An early look at the streamlined Android Developer Console for sideloaded apps. Credit: Read moreHow to…
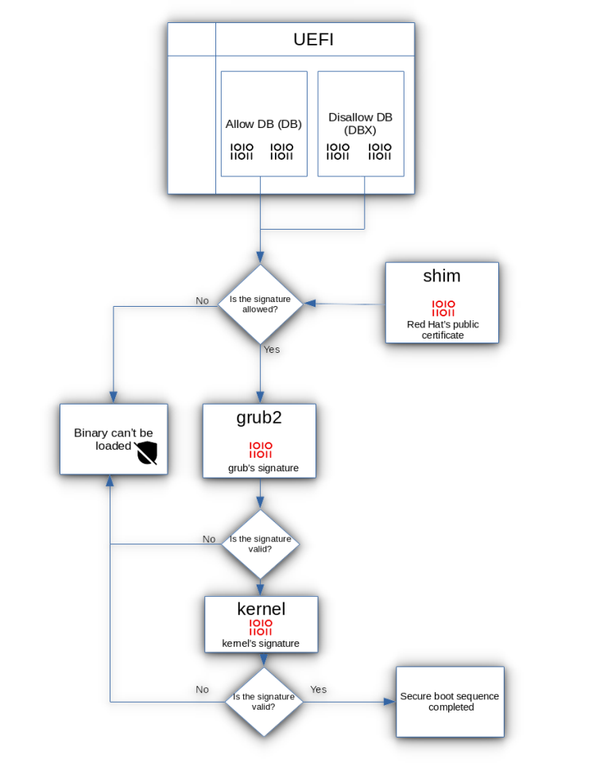
If you’re a Linux user, you might have found yourself tangled in boot issues while installing…
Is your WordPress site running slow, timing out, or crashing altogether? High CPU usage is often…

There is some interesting news from this month’s desktop Linux market share update. Linux has reached…

The hacker ecosystem in Russia, more than perhaps anywhere else in the world, has long blurred…
I have an interesting story to share. You are probably already aware that many products and…
When you browse the internet, install or uninstall software, or just use your computer regularly, you…

Linux is one of the most widely used operating systems in both personal and enterprise environments….
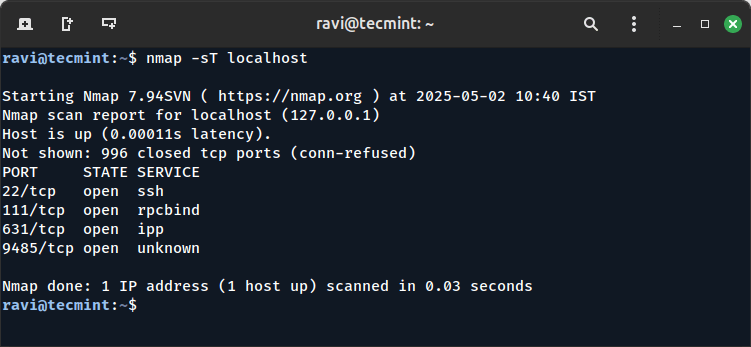
If you’re preparing for a networking, Linux system administration, DevOps, or cybersecurity interview, understanding network ports…
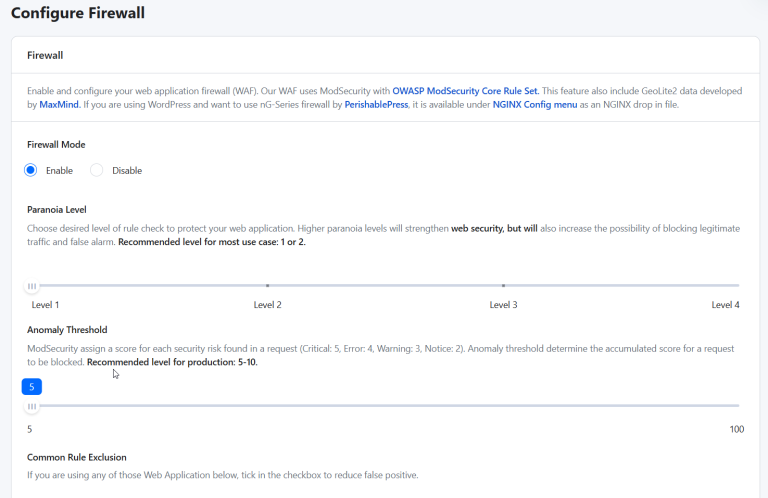
Protecting your WordPress site from vulnerabilities isn’t optional – it’s essential. With WordPress powering over 40%…
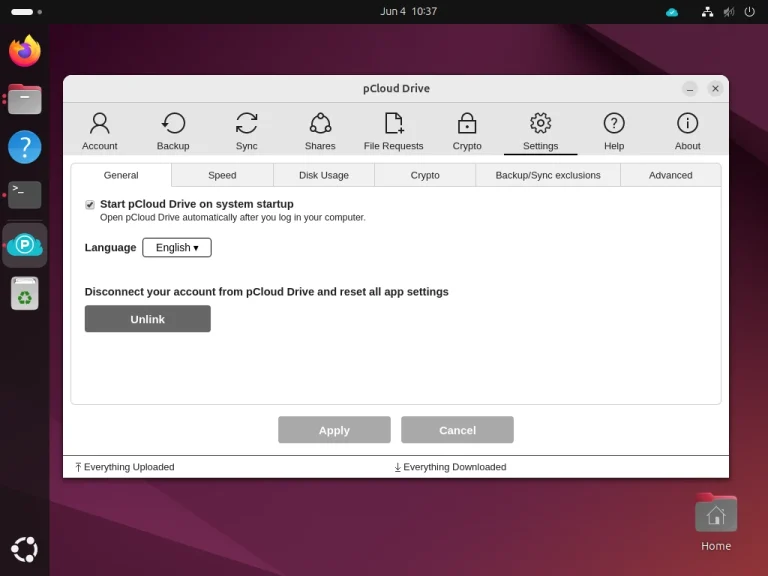
pCloud is a most secure popular cloud storage service that offers a range of features to…