How to fix the ERR_SSL_PROTOCOL_ERROR
Seeing “This site can’t provide a secure connection” with the ERR_SSL_PROTOCOL_ERROR message can stop you in your…
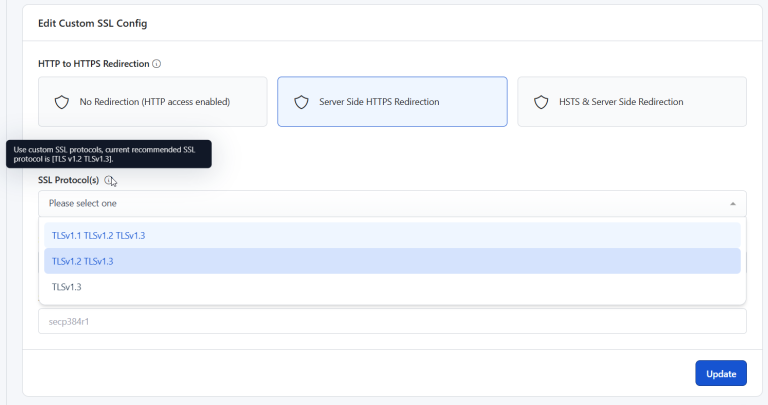
Seeing “This site can’t provide a secure connection” with the ERR_SSL_PROTOCOL_ERROR message can stop you in your…
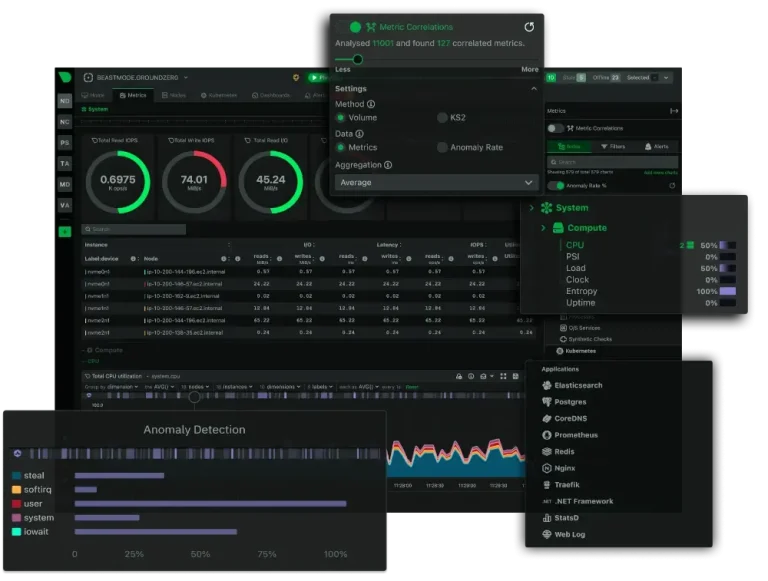
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…
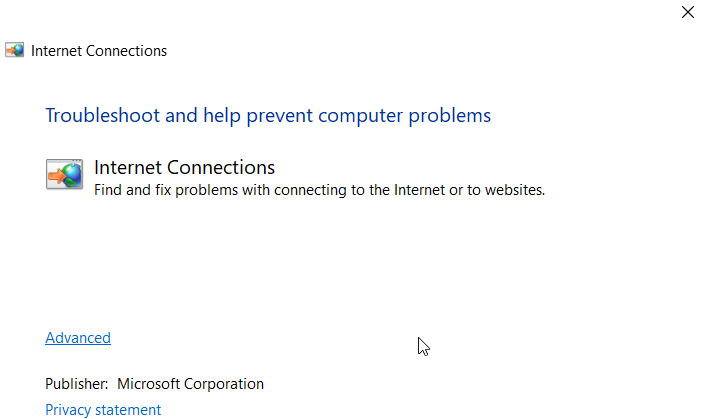
If you use Google Chrome regularly, you’ve probably encountered the dreaded ERR_NETWORK_CHANGED error at least once. One…
If you’re still sending invoices from Word documents, chasing late payments with awkward follow-up emails, or…

An early look at the streamlined Android Developer Console for sideloaded apps. Credit: Read moreHow to…
The recent resistance Academic work on the question of anti-wind farm activism is revealing a pattern:…
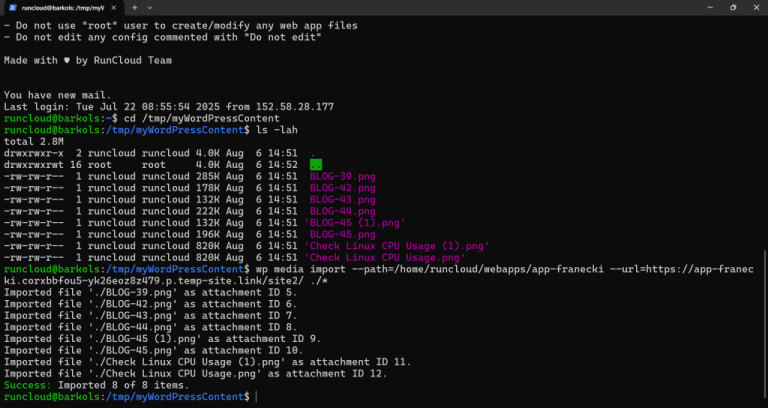
Managing multiple WordPress sites can feel like playing an endless game of dashboard hop – logging…

Beijing is demanding tech companies including Alibaba and ByteDance justify their orders of Nvidia’s H20 artificial…
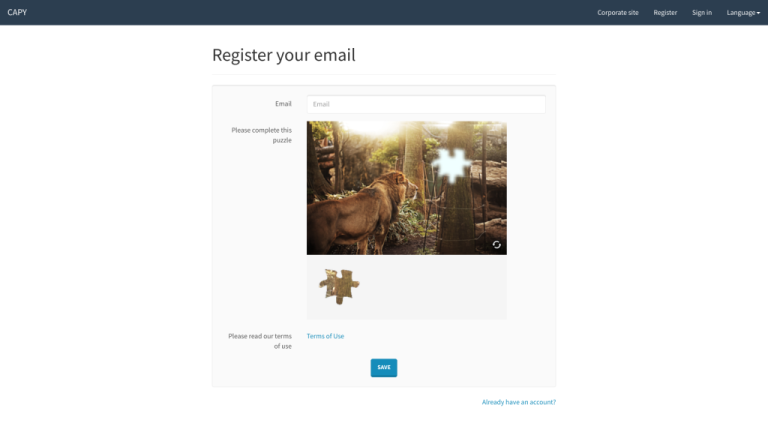
You’ve probably encountered CAPTCHA at some point while browsing the web. It’s that annoying test that…
First, we had “the great decoupling”, now we’re seeing “the great diversification”. Brands are overhauling their…
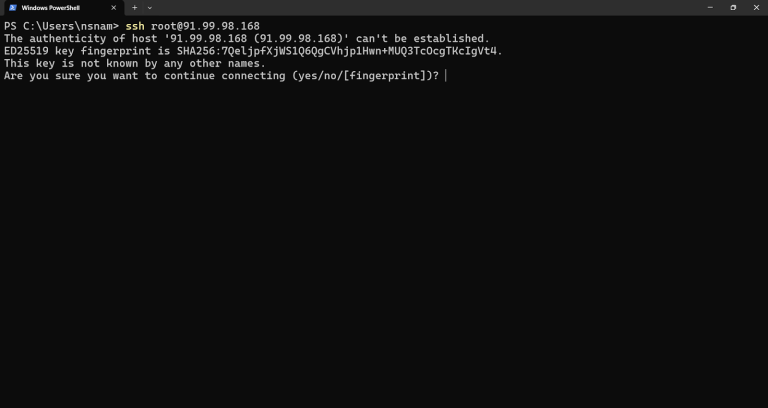
The WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! error will stop you dead in your tracks. Despite looking…
The “Cannot use import statement outside a module” error is a common stumbling block for web…
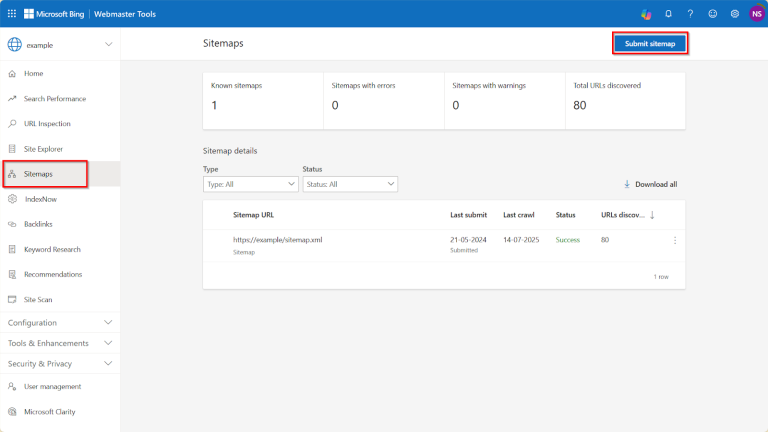
You’ve launched your new website. Now you’re hearing a flood of new terms: SEO, index, sitemap,…
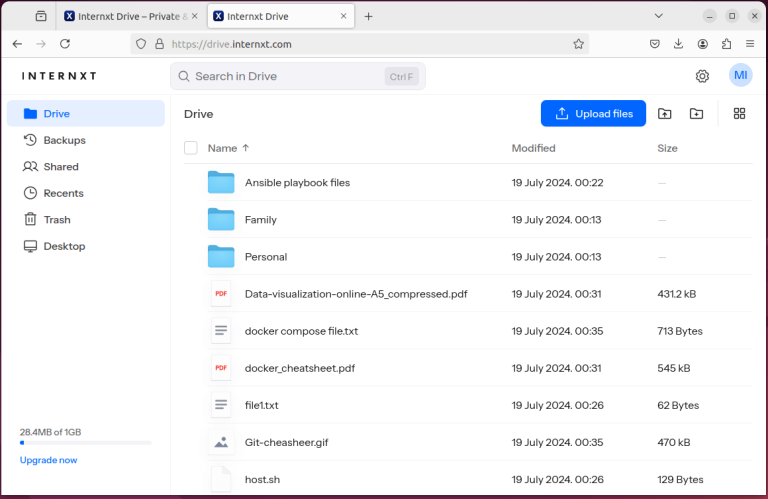
There are countless cloud storage platforms that provide safe and secure storage space for your files….
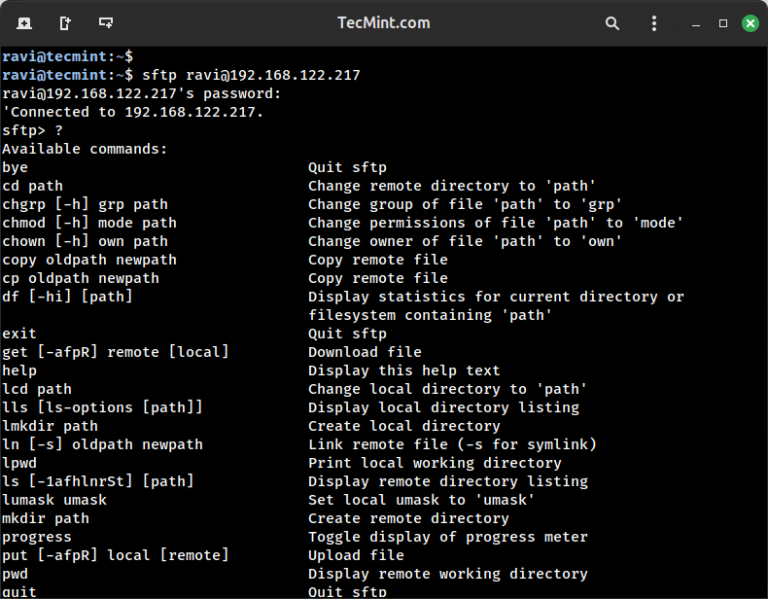
File Transfer Protocol (FTP) was once a widely used method for transferring files or data remotely….
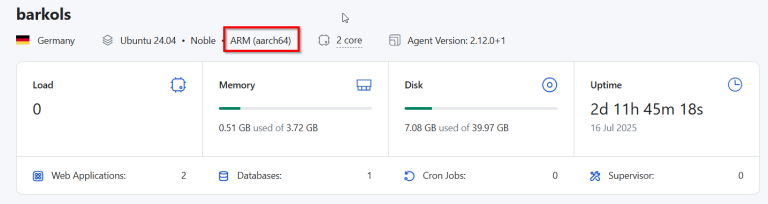
Whether installing new software, following an online tutorial, or troubleshooting an issue, one of the first…