Hashdeep: A Powerful Tool for File Verification in Linux
As a seasoned Linux user with over a decade of experience, I’ve come across many tools…
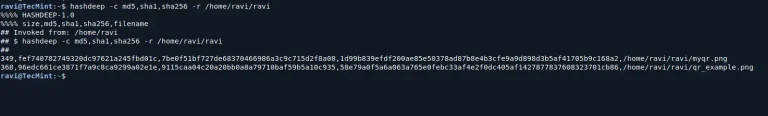
As a seasoned Linux user with over a decade of experience, I’ve come across many tools…
In recent years, AI-driven chatbots like ChatGPT have become popular for tasks such as generating text,…

Amazon now expects around $75 billion in capital spending in 2024, with the majority on technology…

In the past, Katoolin was a script that helped to install Kali Linux tools on your…
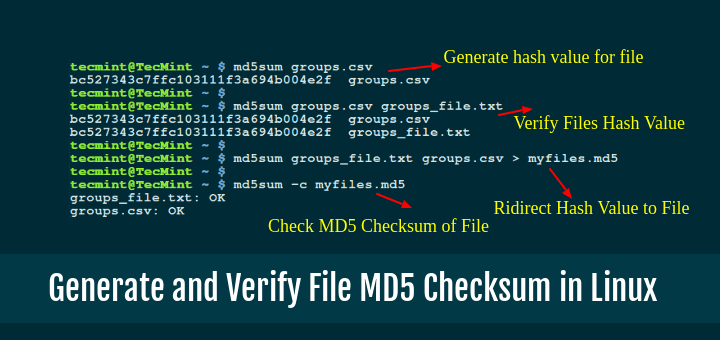
When working with files on Linux, it’s important to ensure their integrity. One way to do…
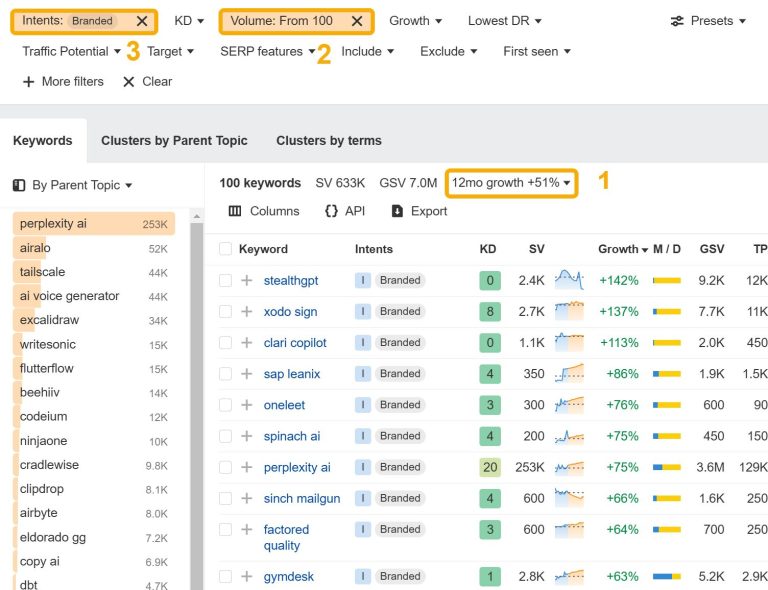
We analyzed the branded search growth of 2,700 software companies to discover the hottest trending startups…
Elasticsearch is a powerful, open-source search engine and analytics platform for storing, searching, and analyzing large…
Change is in the air! And I am not discussing politics here 😉 Read moreHow to…
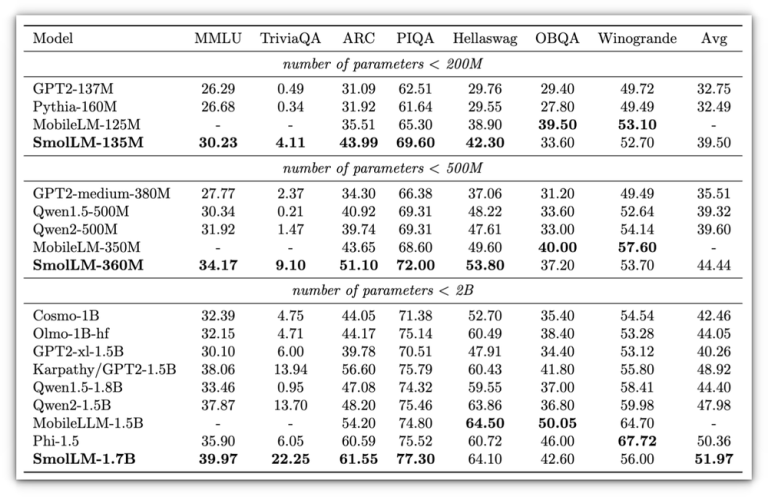
As artificial intelligence continues to weave into our daily lives, there’s a noticeable shift towards smaller,…
Whether in real life or on the internet, security, and privacy are a concern for everyone….
In this scenario, I encourage my patients to move past that initial thought of how awful…
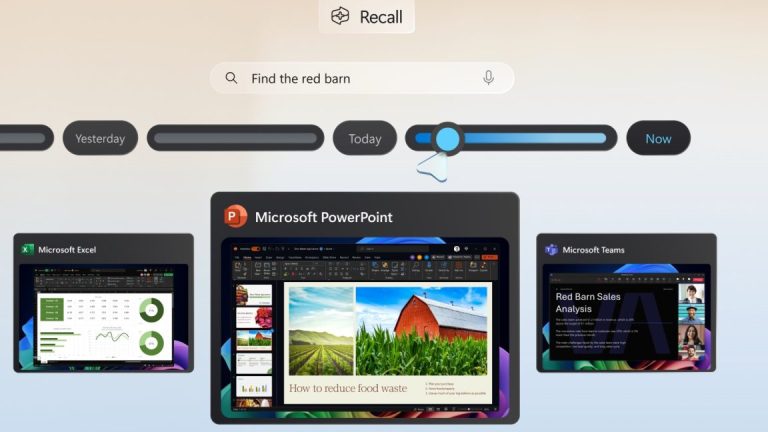
“We are committed to delivering a secure and trusted experience with Recall. To ensure we deliver…
It’s Halloween and it’s time for scary stuff. How about knowing some spooky Linux commands that…

The Vulcan and Atlas V use similar composite payload fairings, both made by Beyond Gravity, the…
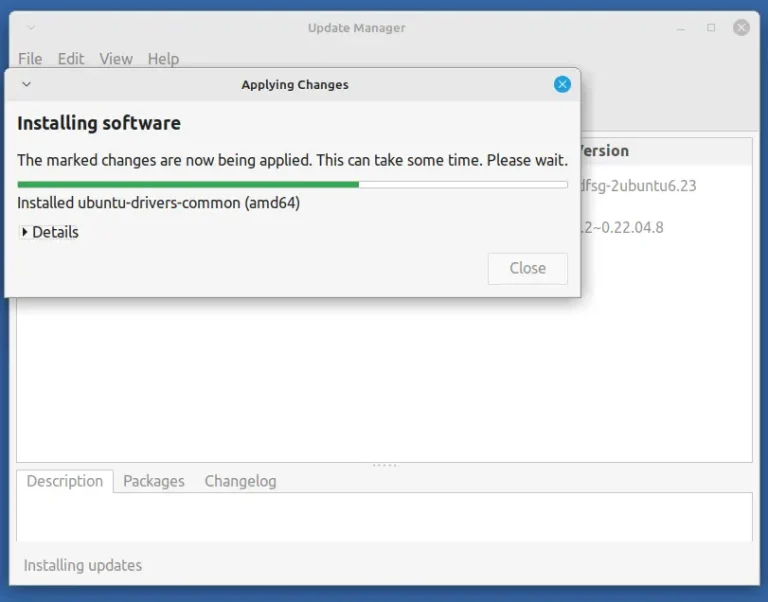
Upgrading your Linux Mint operating system can bring new features, security updates, and improved performance. However,…
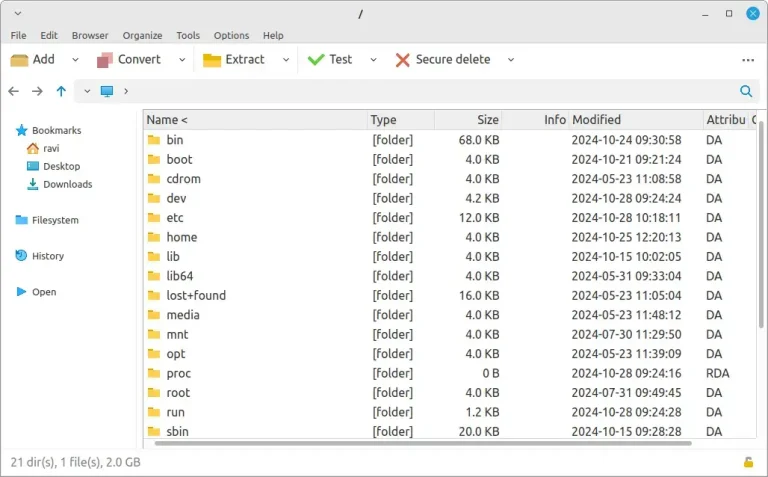
PeaZip is a free and open-source file management tool that works on multiple operating systems, that…