DNF vs. DNF5: Key Differences and Improvements
The Fedora Linux ecosystem has always been at the forefront of adopting cutting-edge technology. One such…

The Fedora Linux ecosystem has always been at the forefront of adopting cutting-edge technology. One such…

‘Tis the season for ❤️ And I would appreciate your love and support in helping us…

Arm and Qualcomm’s dispute over Qualcomm’s Snapdragon X Elite chips is continuing in court this week,…
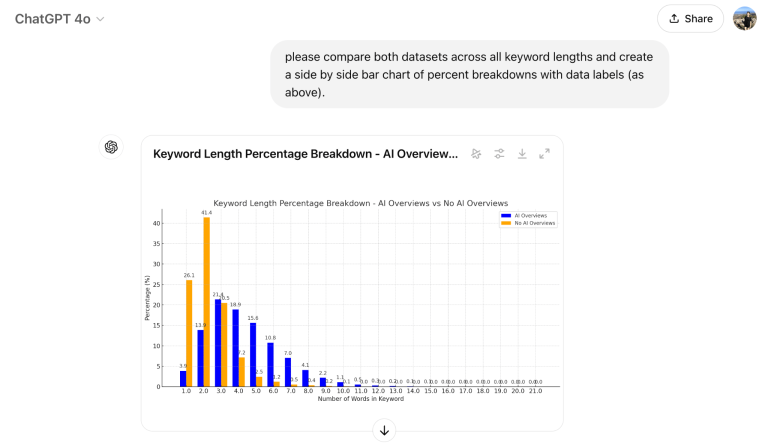
We’re not exactly short on AI content creation tools as we head into 2025—in this list,…
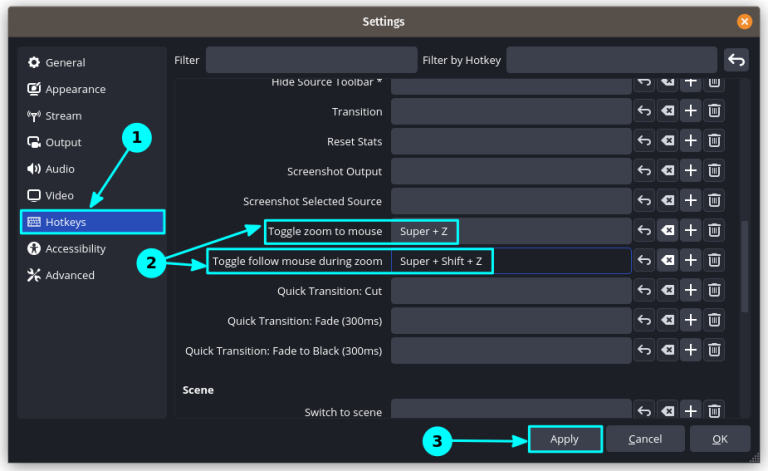
Have you ever wanted to zoom the screen recording area to where your cursor currently is?…
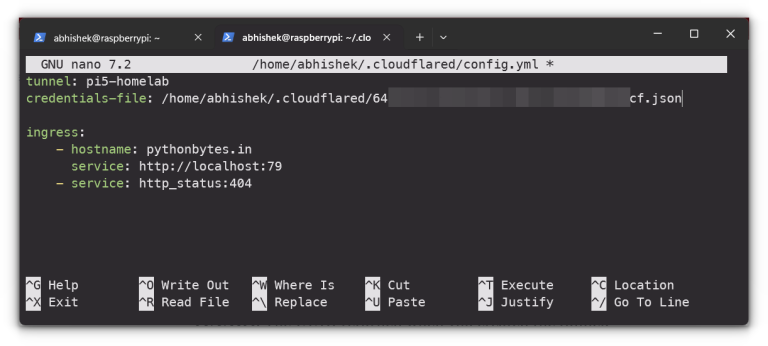
If you’ve ever dipped your toes into self-hosting, you know the struggle is real when it…

Updates for real-time interaction and fine-tuning Developers that make use of OpenAI’s real-time voice APIs will…

We recently concluded Ahrefs Evolve: a sold-out, 2-day, 500-person conference at Pan Pacific Orchard in Singapore….
![How to Fix WordPress Revisions Not Showing [SOLVED]](https://matchpage.info/wp-content/uploads/2024/12/how-to-fix-wordpress-revisions-not-showing-solved-4-768x327.png)
Are your WordPress post revisions not showing? Has your WordPress revisions option suddenly become invisible, or…
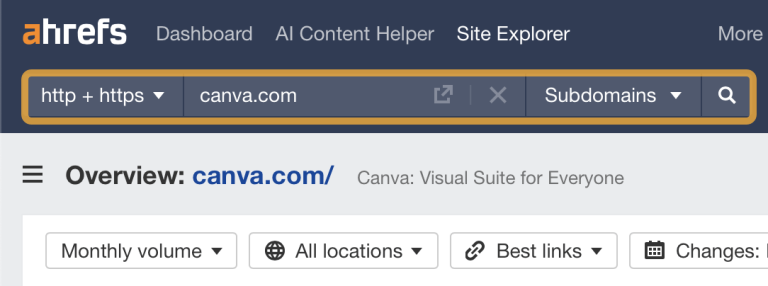
You don’t have to be the next James Bond to start PPC spying—all you need is…
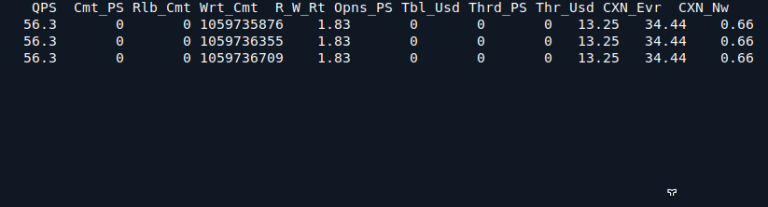
Innotop is an excellent command-line program, similar to the top command, designed to monitor local and…

Fedora is a popular Linux distribution known for its cutting-edge features and stability, making it an…

When Sony launched the PlayStation Portable almost exactly 20 years ago, the value proposition was right…
I have a dual boot system with both Windows and Linux. So, I can switch to…
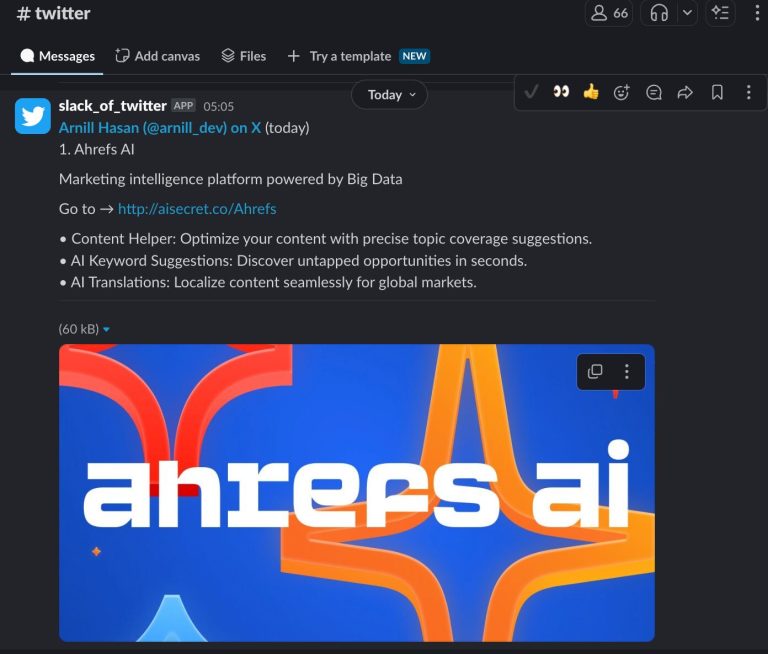
Your phone buzzes, you look down. Someone mentioned your brand on LinkedIn… but not in a…
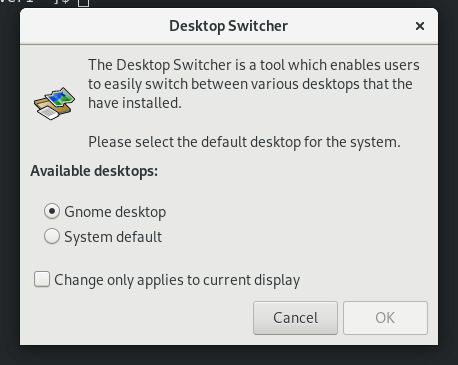
Fedora is a popular Linux distribution known for its cutting-edge features and stability. One of the…