US recommends encrypted messaging as Chinese hackers linger in telecom networks
An unnamed FBI official was quoted in the same report as saying that phone users “would…

An unnamed FBI official was quoted in the same report as saying that phone users “would…
I have tried numerous online tools to keep my life organized, and I constantly look for…
Ghost is a free and open-source blogging platform built with Node.js. As a fast, modern WordPress…
Elasticsearch is a powerful, open-source search engine and analytics platform for storing, searching, and analyzing large…
Whether in real life or on the internet, security, and privacy are a concern for everyone….
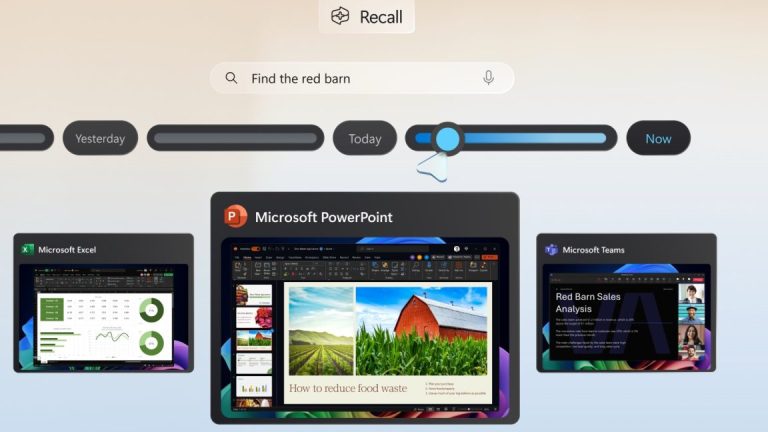
“We are committed to delivering a secure and trusted experience with Recall. To ensure we deliver…
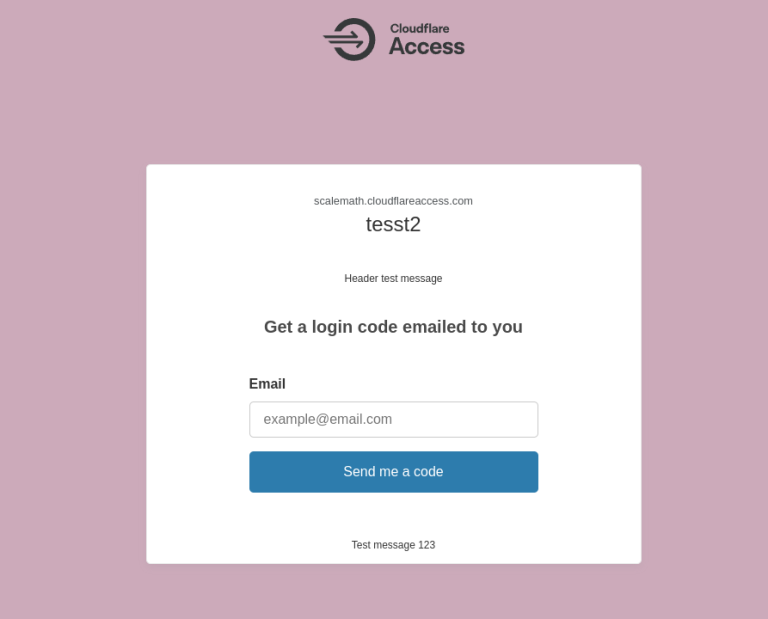
WordPress powers over 40% of all websites on the internet, which makes it a prime target…
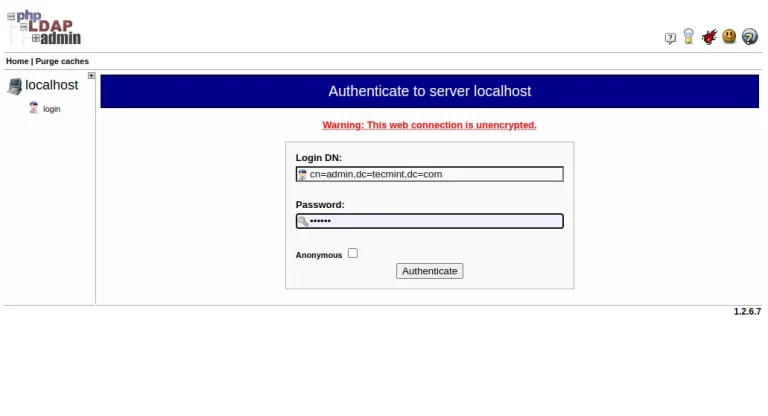
OpenLDAP is an open-source implementation of the Lightweight Directory Access Protocol (LDAP), which provides a way…

The pam_tally2 module, once used to lock user accounts after a certain number of failed SSH…

The .htaccess file is a powerful configuration file used on Apache-based web servers to manage and…
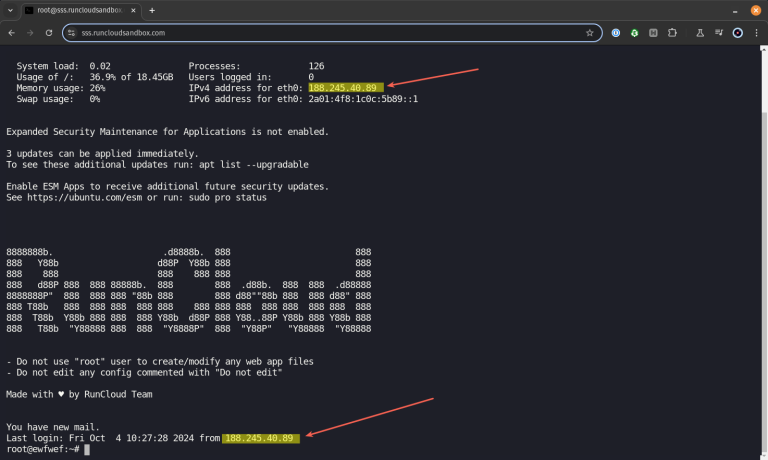
In today’s internet landscape, securing your server from constant threats is vital. It’s inevitable that servers…
Finding the perfect email hosting or newsletter tool can be overwhelming, especially when juggling performance, privacy,…
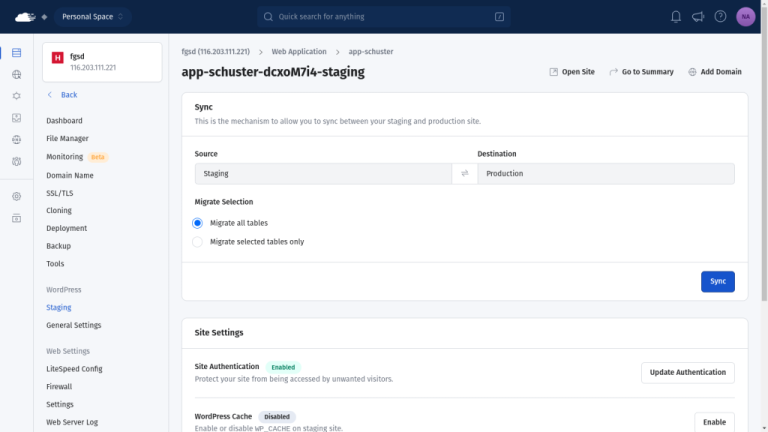
Creating a WordPress staging site is a vital way to test out changes to a website…

Enlarge Getty Images The National Institute of Standards and Technology (NIST), the federal body that sets…
The previous Arch Linux LEMP article just covered basic stuff, from installing network services (Nginx, PHP,…
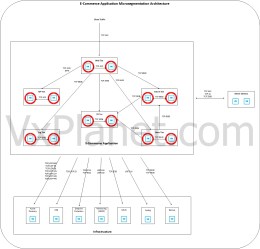
Security Intelligence (formerly NSX Intelligence) is a powerful tool to visualize the security posture of the…